Configuring IDS Policies
An IDS Policy is configured using two tables with "parent-child" type relationship:
| ■ | IDS Policies table ("parent"): Defines a name and provides a description for the IDS Policy. You can configure up to 20 IDS Policies. |
| ■ | IDS Rules table ("child"): Defines the actual rules for the IDS Policy. Each IDS Policy can be configured with up to 20 rules. |
A maximum of 100 IDS rules can be configured (regardless of how many rules are assigned to each policy).
For your convenience, the device provides default IDS Policies which you can use in your deployment if they meet your requirements:
| ■ | "DEFAULT_FEU" - typically suited for far-end users in the WAN. |
| ■ | "DEFAULT_PROXY" - typically suited for proxy servers. |
| ■ | "DEFAULT_GLOBAL" - with global thresholds. |
The following table shows the IDS rules per default IDS Policy:
|
Default IDS Policies and Rules |
Default Values |
||
|---|---|---|---|
|
'Threshold Scope' |
'Threshold Window' |
'Minor-Alarm Threshold' |
|
|
DEFAULT_FEU |
|||
|
Connection abuse |
IP |
30 |
5 |
|
Malformed message |
IP |
30 |
15 |
|
Authentication failure |
IP |
600 |
20 |
|
Dialog establish failure |
IP |
300 |
30 |
|
Abnormal flow |
IP |
30 |
15 |
|
DEFAULT_PROXY |
|
|
|
|
Connection abuse |
IP |
3 |
5 |
|
Malformed message |
IP |
3 |
50 |
|
Authentication failure |
IP |
5 |
30 |
|
Dialog establish failure |
IP |
3 |
50 |
|
Abnormal flow |
IP |
3 |
50 |
|
DEFAULT_GLOBAL |
|
|
|
|
Connection abuse |
Global |
3 |
15 |
|
Malformed message |
Global |
3 |
50 |
|
Authentication failure |
Global |
5 |
30 |
|
Dialog establish failure |
Global |
3 |
50 |
|
Abnormal flow |
Global |
3 |
50 |
| ● | You can edit and delete the default IDS Policies. |
| ● | If the IDS Policies table is empty (i.e., you have deleted all IDS Policies) and you want to restore the default IDS Policies, disable and then enable the IDS feature (see Enabling IDS). |
The following procedure describes how to configure IDS Policies through the Web interface. You can also configure it through ini file or CLI:
| ■ | IDS Policy table: IDSPolicy (ini file) or configure voip > ids policy (CLI) |
| ■ | IDS Rules table: IDSRule (ini file) or configure voip > ids rule (CLI) |
| ➢ | To configure an IDS Policy: |
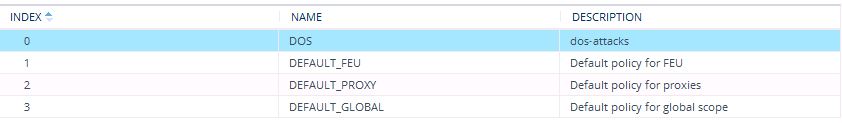
| 1. | Open the IDS Policies table (Setup menu > Signaling & Media tab > Intrusion Detection folder > IDS Policies); the table displays the pre-configured IDS policies: |
| 2. | Click New; the following dialog box appears: |
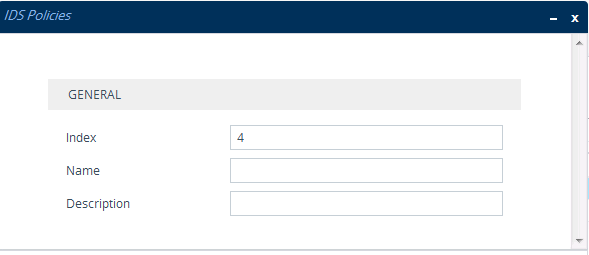
| 3. | Configure an IDS Policy name according to the parameters described in the table below. |
| 4. | Click Apply. |
IDS Policies Table Parameter Descriptions
|
Parameter |
Description |
||||||
|---|---|---|---|---|---|---|---|
|
'Index' policy [Index] |
Defines an index number for the new table row. Note: Each row must be configured with a unique index. |
||||||
|
'Name' rule [Name] |
Defines a descriptive name, which is used when associating the row in other tables. The valid value is a string of up to 40 characters. Note:
|
||||||
|
'Description' description [Description] |
Defines a brief description for the IDS Policy. The valid value is a string of up to 100 characters. |
| 5. | In the IDS Policies table, select the required IDS Policy row, and then click the IDS Rule link located below the table; the IDS Rule table opens. |
| 6. | Click New; the following dialog box appears: |
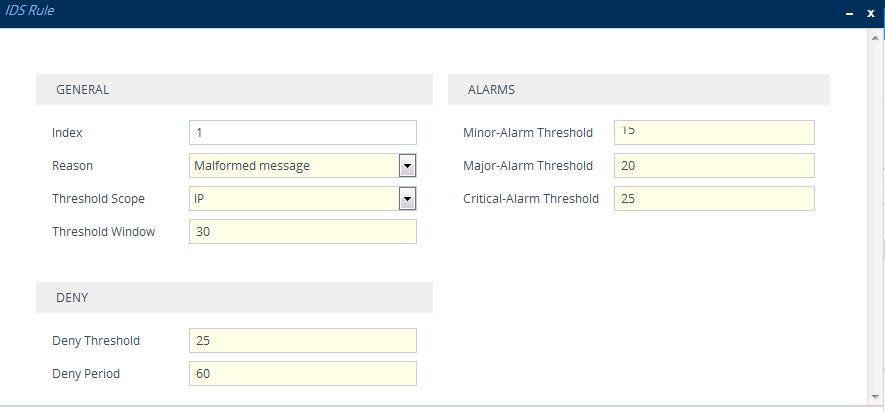
The figure above shows a configuration example: If 15 malformed SIP messages ('Reason') are received within a period of 30 seconds ('Threshold Window'), a minor alarm is sent ('Minor-Alarm Threshold'). Every 30 seconds, the rule’s counters are cleared ('Threshold Window'). If more than 25 malformed SIP messages are received within this period, the device blocks for 60 seconds the remote IP host ('Deny Threshold') from where the messages were received.
| 7. | Configure an IDS Rule according to the parameters described in the table below. |
| 8. | Click Apply, and then save your settings to flash memory. |
IDS Rule Table Parameter Descriptions
|
Parameter |
Description |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| General | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Index' rule-id [IDSRule_RuleID] |
Defines an index number for the new table record. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Reason' reason [IDSRule_Reason] |
Defines the type of intrusion attack (malicious event).
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Threshold Scope' threshold-scope [IDSRule_ThresholdScope] |
Defines the source of the attacker to consider in the device's detection count.
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Threshold Window' threshold-window [IDSRule_ThresholdWindow] |
Defines the threshold interval (in seconds) during which the device counts the attacks to check if a threshold is crossed. The counter is automatically reset at the end of the interval. The valid range is 1 to 1,000,000. The default is 1. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Alarms |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Minor-Alarm Threshold' minor-alrm-thr [IDSRule_MinorAlarmThreshold] |
Defines the threshold that if crossed a minor severity alarm is sent. The valid range is 1 to 1,000,000. A value of 0 or -1 means not defined. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Major-Alarm Threshold' major-alrm-thr [IDSRule_MajorAlarmThreshold] |
Defines the threshold that if crossed a major severity alarm is sent. The valid range is 1 to 1,000,000. A value of 0 or -1 means not defined. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Critical-Alarm Threshold' critical-alrm-thr [IDSRule_CriticalAlarmThreshold] |
Defines the threshold that if crossed a critical severity alarm is sent. The valid range is 1 to 1,000,000. A value of 0 or -1 means not defined. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Deny |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Deny Threshold' deny-thr [IDSRule_DenyThreshold] |
Defines the threshold that if crossed, the device blocks the remote host (attacker). The default is -1 (i.e., not configured). To view the IDS blocked list, see Viewing IDS Active Blocked List. Note: The parameter is applicable only if the 'Threshold Scope' parameter is set to IP or IP+Port. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
'Deny Period' deny-period [IDSRule_DenyPeriod] |
Defines the duration (in sec) to keep the attacker on the blocked list, if configured using the 'Deny Threshold' parameter. The valid range is 0 to 1,000,000. The default is -1 (i.e., not configured). To view the IDS blocked list, see Viewing IDS Active Blocked List. Note: The parameter is applicable only if the 'Threshold Scope' parameter is set to IP or IP+Port. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||